Vulnerable perimeter devices: a huge attack surface
By A Mystery Man Writer

With the increase of critical gateway devices deployed to support off-premise work, companies across the world have to adapt to a new threat landscape where perimeter and remote access devices are now in the first line.

The Hidden Attack Surface That's Growing Out of Control
Top 5 Vulnerability Management Tools
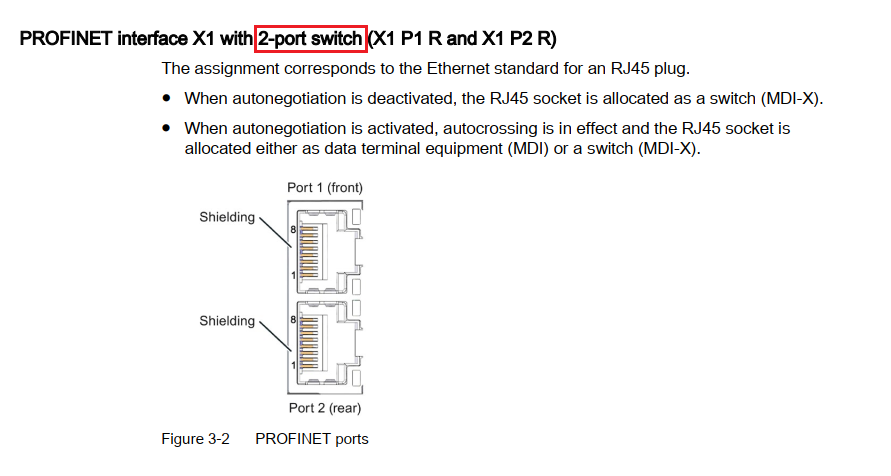
SCADAfence Archives - Page 9 of 10 - Version 2 Limited

The human attack surface – an underestimated cyber security threat

Latest Remote Desktop news
External Attack Surface Management. What are you missing out on?

A Guide To Digital Risk Protection For Security Teams – Momentum Cyber

2020 Archives - Page 8 of 16 - Version 2 Limited
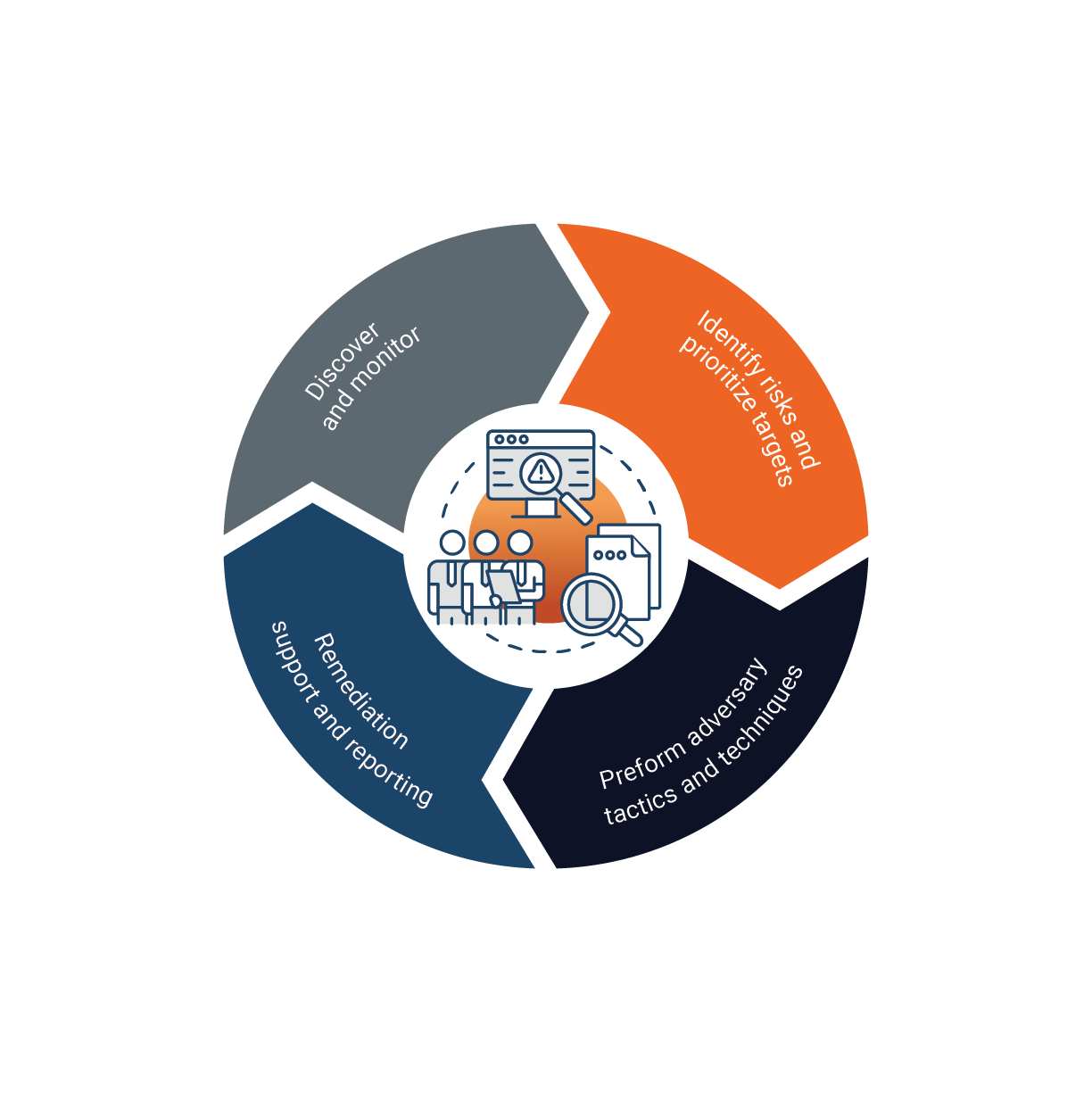
EMBER's Attack Surface Management (ASM) Services







