Length extension attack. What is length extension?
When a Merkle-Damgård based hash is misused as a message authentication code with construction H(secret ‖ message), and message and the length of secret is known, a length extension attack allows…
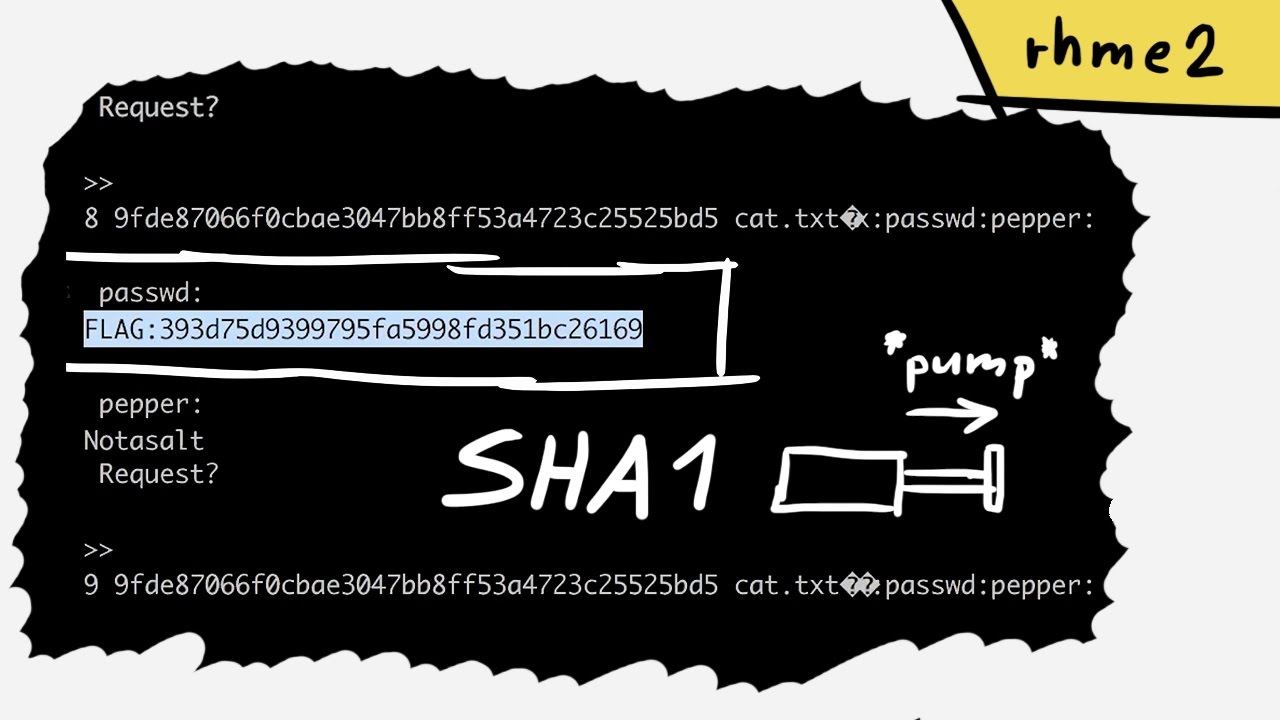
SHA1 length extension attack on the Secure Filesystem - rhme2 Secure Filesystem (crypto 100)

PPT - Workshop 2: Length Extension Attack PowerPoint Presentation, free download - ID:1618604
SANS Penetration Testing, Modern Web Application Penetration Testing Part 2, Hash Length Extension Attacks
Length extension attack. What is length extension?, by Deep RnD

How did length extension attacks made it into SHA-2?

Length extension attack - Wikipedia.pdf - Length extension attack In cryptography and computer security a length extension attack is a type of attack
GitHub - PortSwigger/length-extension-attacks: Length extension attacks in Burp Suite
Solved A main threat to the Merkle-Damgard construction is

哈希长度拓展攻击(Hash Length Extension Attacks)

Guest Post by SlowMist: The Hidden Risks of Hash Functions: Length Extension Attacks and Server-Side Security Vulnerabilities

Name and technical properties of the most popular hash functions

hash - Why HAIFA and sponge constructions are not prone to length extension attacks? - Cryptography Stack Exchange

Solved (10 Points) A server is susceptible to a hash length

Dead Ends in Cryptanalysis #1: Length Extension Attacks - Dhole Moments
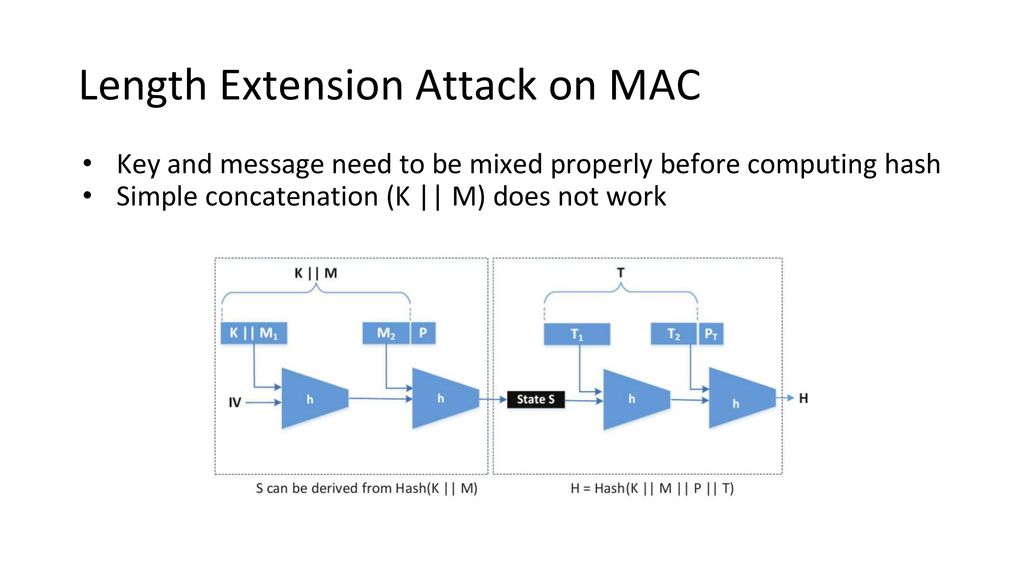
One-Way Hash Functions - ppt download







